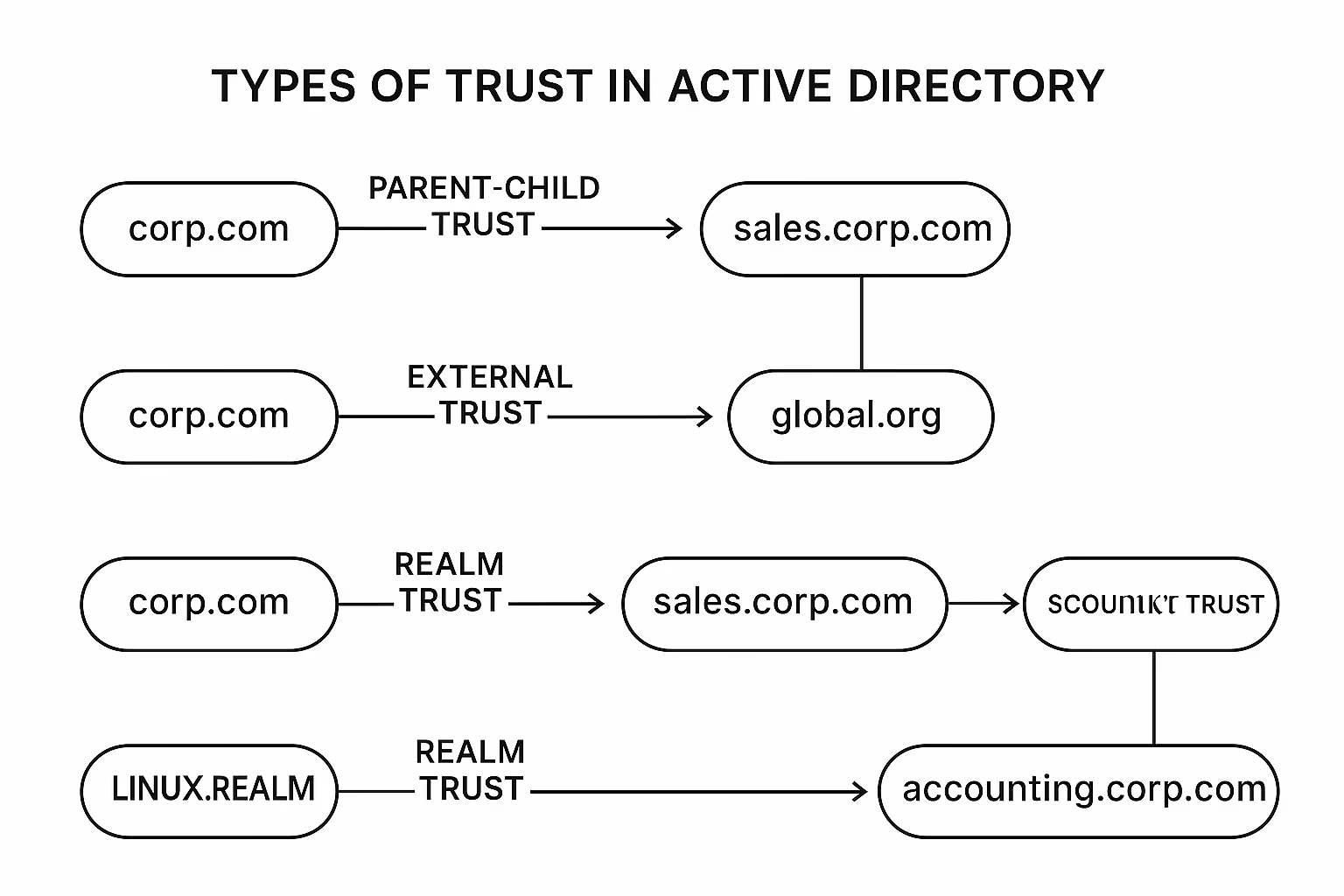
1. Parent-Child Trust
- Type: Transitive, Two-way, Automatic
- When it is created: Automatically created when you add a child domain to a parent domain (e.g., creating a subdomain).
- Behavior:
- Users in the child domain can access resources in the parent domain and vice versa.
- Trust is transitive: if Domain A trusts Domain B, and Domain B trusts Domain C, then Domain A trusts Domain C.
Example:corp.com → child domain sales.corp.com
2. Tree-Root Trust
- Type: Transitive, Two-way, Automatic
- When it is created: Automatically created when you add a new tree to an existing forest.
- Behavior:
- Domains in different trees within the same forest trust each other automatically.
- Helps in hierarchical and structured domain naming.
Example:
Tree 1: corp.com ↔ Tree 2: marketing.net (both in the same forest)
3. External Trust
- Type: Non-transitive, One-way or Two-way, Manual
- When it is created: Created manually when you need to trust a domain outside your forest (especially if that domain is from an older NT 4.0 domain or different forest without forest trust).
- Behavior:
- Non-transitive: Only the two domains trust each other; it doesn’t extend beyond them.
- Useful for interoperability with legacy systems.
Example:corp.com ↔ legacydomain.local (old Windows NT4 or standalone domain)
4. Forest Trust
- Type: Transitive, One-way or Two-way, Manual
- When it is created: Manually created between two forests (root domains).
- Behavior:
- Allows all domains in one forest to trust all domains in another forest.
- Can be one-way (A trusts B) or two-way (both trust each other).
- Requires both forests to be at Forest Functional Level 2003 or higher.
Example:
Forest A: corp.com ↔ Forest B: global.org
5. Realm Trust
- Type: Transitive or Non-transitive, One-way or Two-way, Manual
- When it is created: Created to establish a trust between an Active Directory domain and a non-Windows Kerberos realm (like a UNIX/Linux Kerberos v5 realm).
- Behavior:
- Can be either one-way or two-way.
- Can be transitive or non-transitive depending on how it’s configured.
- Helps integration between Windows and non-Windows environments.
Example:
AD Domain: corp.com ↔ Kerberos Realm: LINUX.REALM
6. Shortcut Trust
- Type: Transitive, One-way or Two-way, Manual
- When it is created: Manually created between domains in the same forest to speed up authentication.
- Behavior:
- Reduces authentication time when users in one domain need to access resources in another distant domain (in a deep or complex domain tree).
- Helps avoid the default trust path and optimize performance.
Example:
Instead of: user.sales.corp.com → corp.com → accounting.corp.com,
you can create a shortcut directly betweensales.corp.com ↔ accounting.corp.com.
Quick Summary Table:
| Trust Type | Transitive | Direction | Created How | Purpose |
|---|---|---|---|---|
| Parent-Child | Yes | Two-way | Automatic | Child domain trust |
| Tree-Root | Yes | Two-way | Automatic | Trust between trees in a forest |
| External | No | One or Two-way | Manual | Trust external domains (legacy/single) |
| Forest | Yes | One or Two-way | Manual | Trust between different forests |
| Realm | Yes/No | One or Two-way | Manual | Trust with non-Windows Kerberos systems |
| Shortcut | Yes | One or Two-way | Manual | Optimize trust paths inside a forest |
