Passkeys are a technology for logging into websites and applications without a password using a private and public key pair. The server does not store any critical data that could be stolen and the passkey is also tied to a device. M365 now supports this method as well. When users…

Diskless Solution
CCBoot is a diskless boot system that will make all of your PCs like new after every single reboot. This means, no more worrying about Spyware, Viruses, and Trojans. Every single time a PC is rebooted, it’s wiped clean, leaving you with the feeling of a fresh install after every…

How to Publish an App on Microsoft Store: A Step-by-Step Guide
Publishing an app on the Microsoft Store can be a rewarding experience, whether you’re a student looking to showcase your coding skills, an individual exploring app development, or a hobbyist turning a passion project into something more. The Microsoft Store offers a platform to distribute your app to millions of…
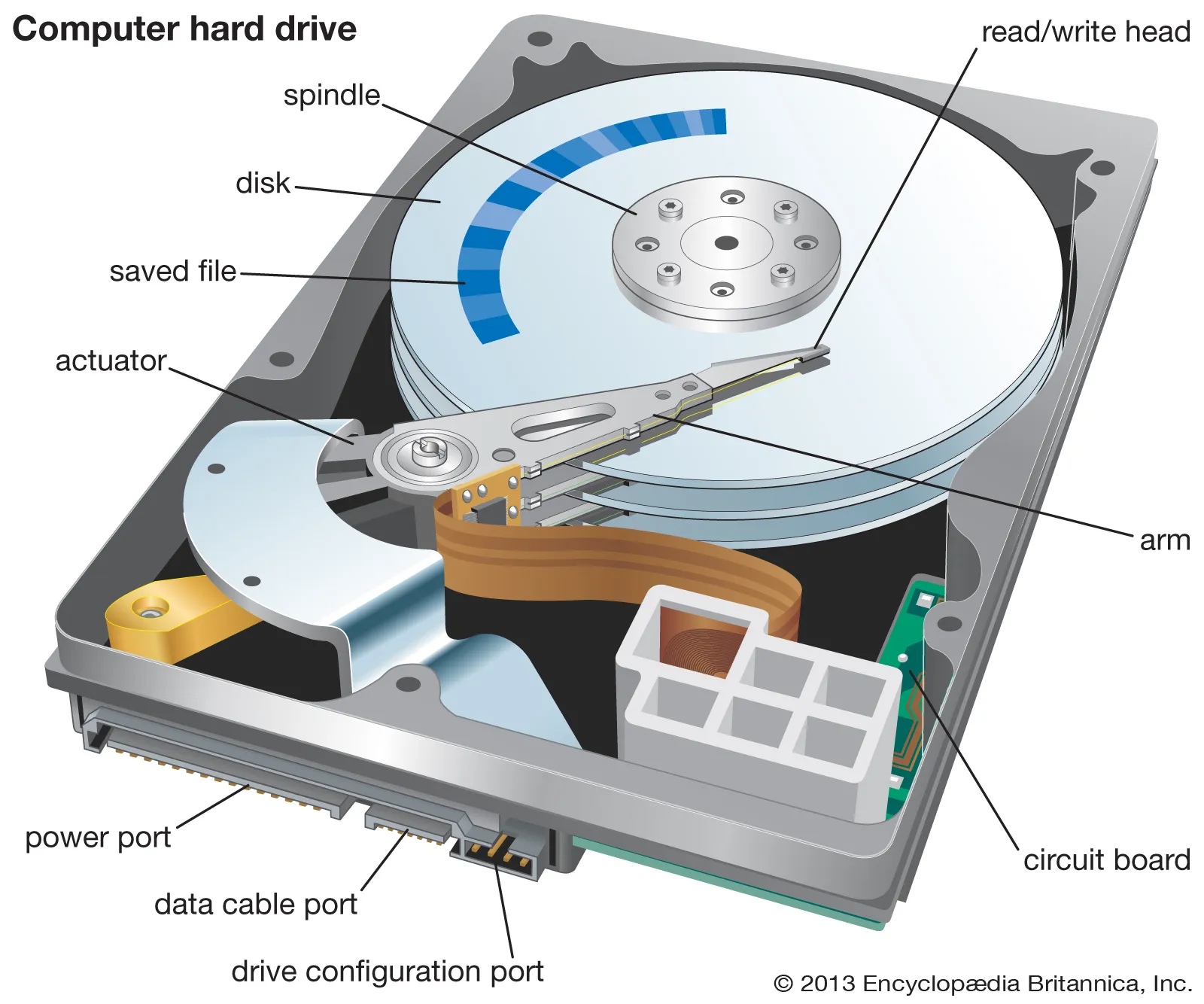
How to clone the drive in your Windows computer
When installing a new drive in your computer, you have two (2) options: perform a fresh installation of the operating system and all the programs. Or you can clone the current drive to the new one and preserve the installed operating system and programs. Since many people do not remember…
How to close an unresponsive app in Windows
We’ve all been there. You’re working on an important document or playing your favorite game, and suddenly, the application freezes. The window becomes unresponsive; no matter how much you click or tap, it just sits there. While it’s frustrating, there are several methods you can use to close unresponsive applications…

Apps Like Uber, Ola Charge You More Based on Your Battery Percentage?
Ride-sharing apps like Uber, Ola, and Rapido have transformed the way we travel. However, concerns about how these apps access and use sensitive information have been the subject of intense debate. One recurring claim is that these apps may charge users more when their phone’s battery level is low. While…

Anonymize Your Traffic With Proxychains & Tor: A Comprehensive Guide
In an era where digital privacy is increasingly under threat, individuals seek effective means to safeguard their online activities from prying eyes. One such powerful tool for anonymity is the combination of Proxychains and Tor. This blog post will guide you through the installation process on Linux, Mac, Windows, and…
