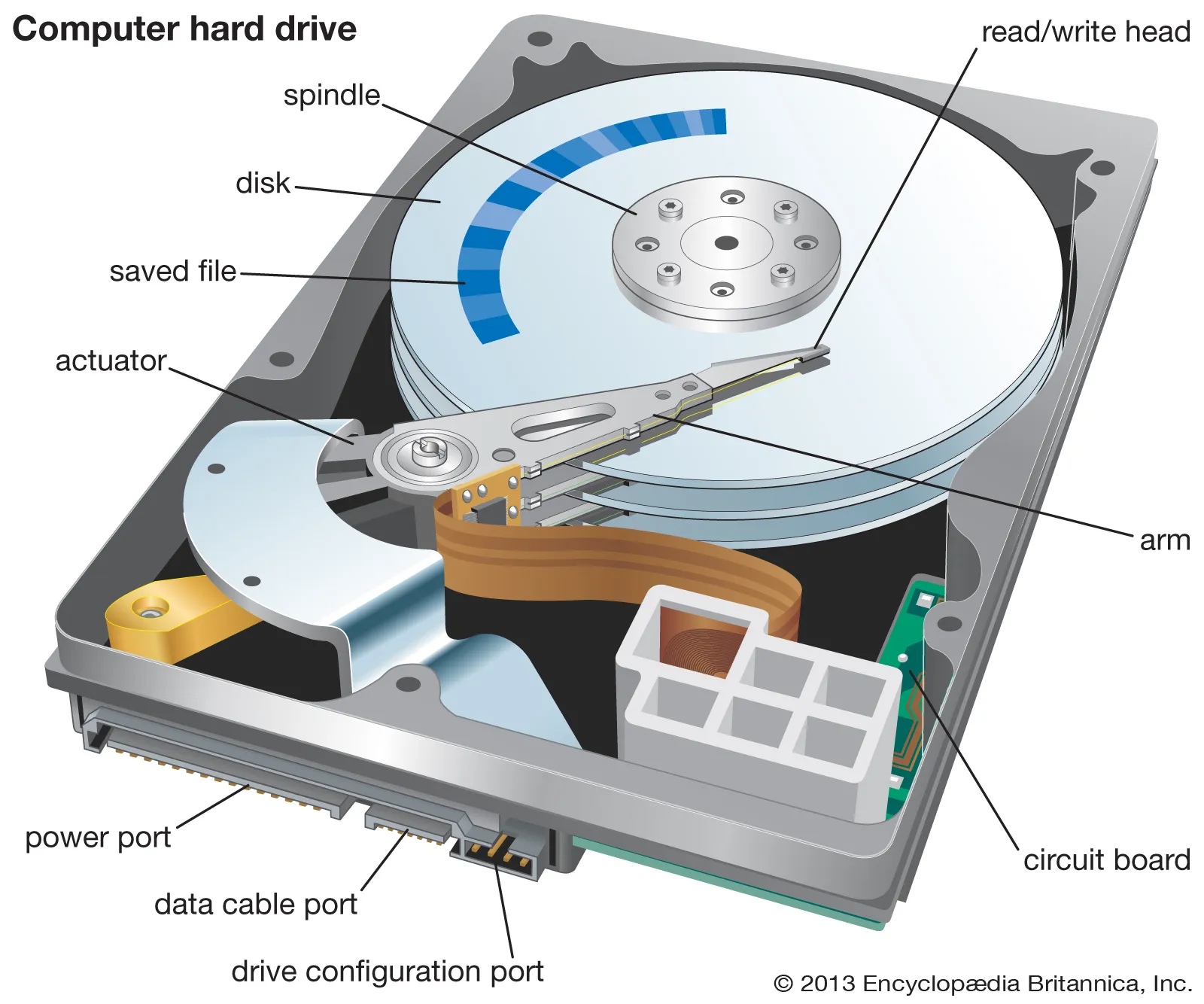
When you delete a file on your computer, whether through the Recycle Bin on Windows or rm on Linux, the data isn’t actually erased. Instead, the operating system marks the space the file occupies as “free” and available for new data, while the original file content remains intact. This means that with the right tools, that “deleted” file can often be recovered.
To truly delete a file beyond recovery, you need to take extra steps, such as overwriting the file’s data multiple times. In this blog post, we’ll explore several methods and tools—both built-in and third-party—for ensuring data is permanently erased and cannot be recovered.
Why Regular Deletion Isn’t Enough
When you delete a file:
- The file system only removes the reference (pointer) to the file.
- The actual data is left on the disk until it gets overwritten by new data.
- This means the file can be recovered using specialized recovery software until the disk sectors are overwritten.
Data Recovery Tools: How Deleted Files Can Be Recovered
Before diving into secure deletion methods, let’s quickly touch on how deleted files can be recovered. Recovery software scans the unallocated space on your drive for data remnants and can often piece together “deleted” files. Here are some popular data recovery tools:
- Recuva: A free and easy-to-use tool for recovering deleted files on Windows.
- TestDisk & PhotoRec: Open-source tools for recovering lost files from hard drives, memory cards, and more.
- EaseUS Data Recovery Wizard: Available in both free and paid versions, it’s user-friendly and capable of recovering files from various devices.
Secure Deletion Methods
To prevent recovery tools from accessing your deleted data, you must overwrite it. This process ensures the data is truly gone. Below are some of the most effective methods for securely deleting files and wiping free space.
1. Using the cipher /w Command (Windows)
Windows comes with a built-in tool called cipher that can securely wipe unallocated (free) space on a drive by overwriting it. This prevents deleted files from being recovered.
How to Use cipher /w:
- Open Command Prompt as an Administrator.
- Run the following command to wipe free space on the C drive:
| 1 | cipher /w:C:\ |
Replace C:\ with the drive letter where you want to wipe free space. This command will overwrite all free space on the drive with random data, ensuring that deleted files cannot be recovered. Importantly, this doesn’t touch existing files—only free space is wiped.
2. Using sdelete (Sysinternals)
Sysinternals’ sdelete is a more advanced Windows tool for securely deleting files and wiping free space. It was designed to work with both HDDs and SSDs.
How to Use sdelete:
- Download
sdeletefrom Sysinternals. - Open Command Prompt as an Administrator.
- To securely wipe free space, use:
| 1 | sdelete -z C:\ |
This command zeros out the free space on the C: drive, making recovery of deleted files nearly impossible. You can also use -p to specify how many passes (overwrites) you want for increased security.
Example:
| 1 | sdelete -p 3 C:\ |
This performs 3 overwrite passes for greater security.
3. Using shred (Linux)
On Linux systems, the shred command is a powerful tool for securely deleting files by overwriting them multiple times with random data.
How to Use shred:
- To securely delete a file:
| 1 | shred -u -n 3 filename |
The -n 3 option overwrites the file 3 times (you can change this number for more passes), and the -u flag removes the file after shredding it.
- To wipe an entire drive:
| 1 | shred -vfz /dev/sda |
This overwrites the entire /dev/sda drive with random data, then zeros it out (-z), ensuring no data can be recovered.
Why Multiple Passes?
While one overwrite is often enough to make data recovery extremely difficult, some sensitive data may benefit from additional passes for increased security. Tools like shred and sdelete allow you to customize the number of overwrites.
4. Third-Party Tools for Secure Deletion
If you’re not comfortable using command-line tools or need additional features, there are several reliable third-party tools designed for secure deletion.
For Windows:
- Eraser: A free tool that lets you securely delete individual files or wipe entire disk partitions.
- CCleaner: Offers a secure file deletion feature in its “Tools” section, where you can wipe free space or delete specific files securely.
- BleachBit: A free tool that works on both Windows and Linux for securely deleting files and wiping free space.
For Mac:
- FileShredder: This tool is specifically designed for macOS, allowing users to securely delete files.
- Permanent Eraser: A simple macOS tool for securely deleting files using the same method as
shred.
5. Special Considerations for SSDs
Solid-state drives (SSDs) handle data differently than traditional hard drives (HDDs) due to wear-leveling mechanisms that distribute writes across the drive. This makes traditional file overwriting tools less effective for SSDs. However, most modern SSDs come with built-in secure erase features.
TRIM Command for SSDs
Most SSDs support the TRIM command, which allows the operating system to inform the SSD which blocks of data are no longer in use and can be securely wiped. Windows and Linux automatically handle TRIM if the SSD is properly configured.
For more thorough deletion, you can use tools like:
- Parted Magic: Includes an SSD secure erase tool.
- Manufacturer Tools: Many SSD manufacturers provide secure erase utilities, such as Samsung Magician or Intel SSD Toolbox.
6. Physical Destruction
For the most sensitive data, the ultimate solution is physically destroying the drive. This method is often used by governments and corporations dealing with highly classified data.
- Hard Drives (HDDs): You can drill holes through the drive platter or use a specialized hard drive shredder.
- Solid-State Drives (SSDs): SSDs should be destroyed by crushing or shredding, as they store data in chips rather than platters.